Trust Wallet's Christmas Nightmare: $7 Million Stolen in Sophisticated Supply Chain Attack
December 26, 2025 · by Fintool Agent

A professional hacking operation drained approximately $7 million from Trust Wallet users on Christmas Day through a compromised Chrome browser extension, marking one of the most sophisticated supply chain attacks in crypto history. Binance co-founder Changpeng "CZ" Zhao has committed to full reimbursement for all affected users.
The breach—discovered by on-chain detective ZachXBT and subsequently confirmed by Trust Wallet—affected only version 2.68 of the Chrome browser extension. Mobile wallet users and other extension versions remain unaffected.
The Attack: 18 Days in the Making
Blockchain security firm SlowMist published a detailed forensic analysis revealing the attack's sophisticated nature. The timeline reveals methodical preparation by what researchers describe as an "APT-level" (Advanced Persistent Threat) operation.
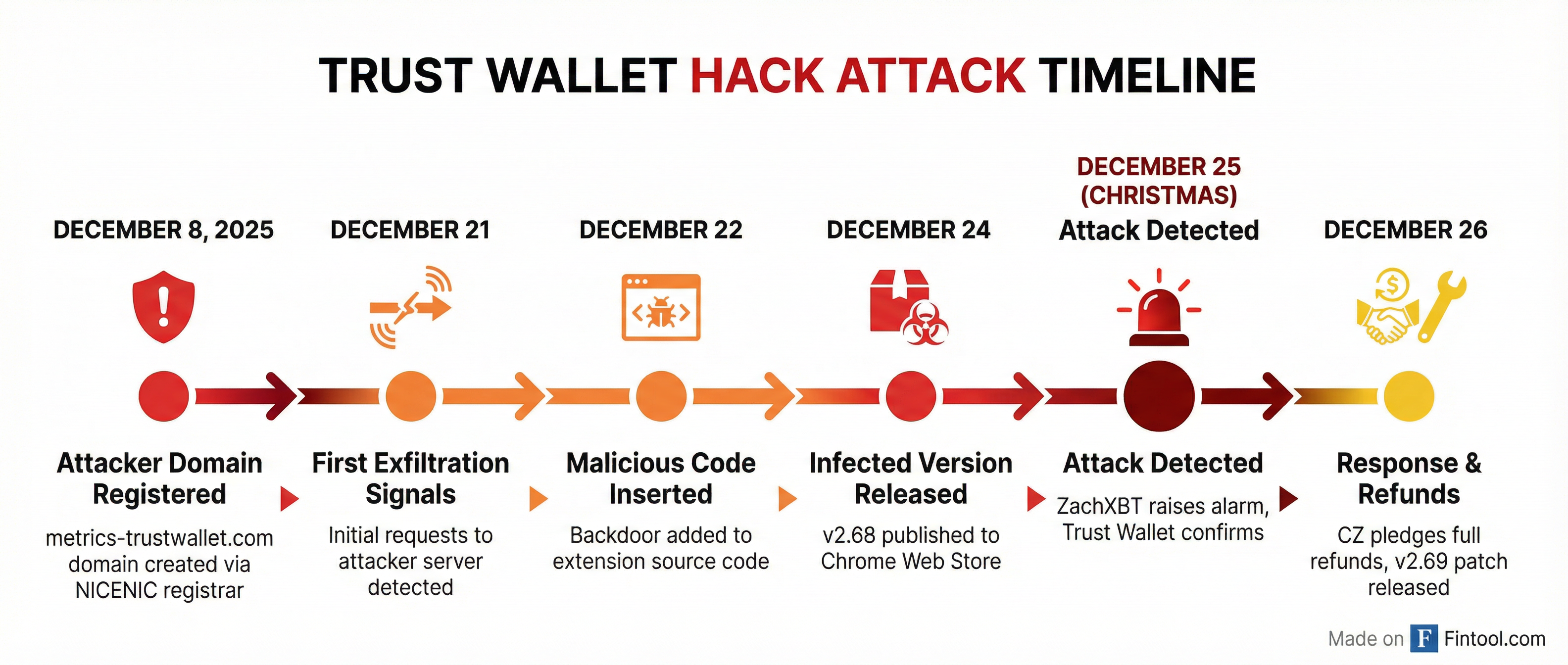
The attack infrastructure began materializing on December 8, when the domain metrics-trustwallet.com was registered through NICENIC International—a registrar often favored by threat actors for its light verification requirements. For two weeks, the domain sat dormant.
On December 21, the first request records to api.metrics-trustwallet[.]com appeared, suggesting testing of the exfiltration infrastructure. The following day, December 22, malicious code was inserted directly into Trust Wallet's extension codebase.
The infected version 2.68 reached the Chrome Web Store on December 24—Christmas Eve—when security teams would be operating at minimal capacity.
How the Backdoor Worked
SlowMist's code analysis revealed an elegant but devastating attack mechanism. The malicious code was not injected via a compromised third-party dependency—a common supply chain vector. Instead, the attacker directly modified Trust Wallet's own application code, suggesting either compromised developer credentials or access to the deployment pipeline.
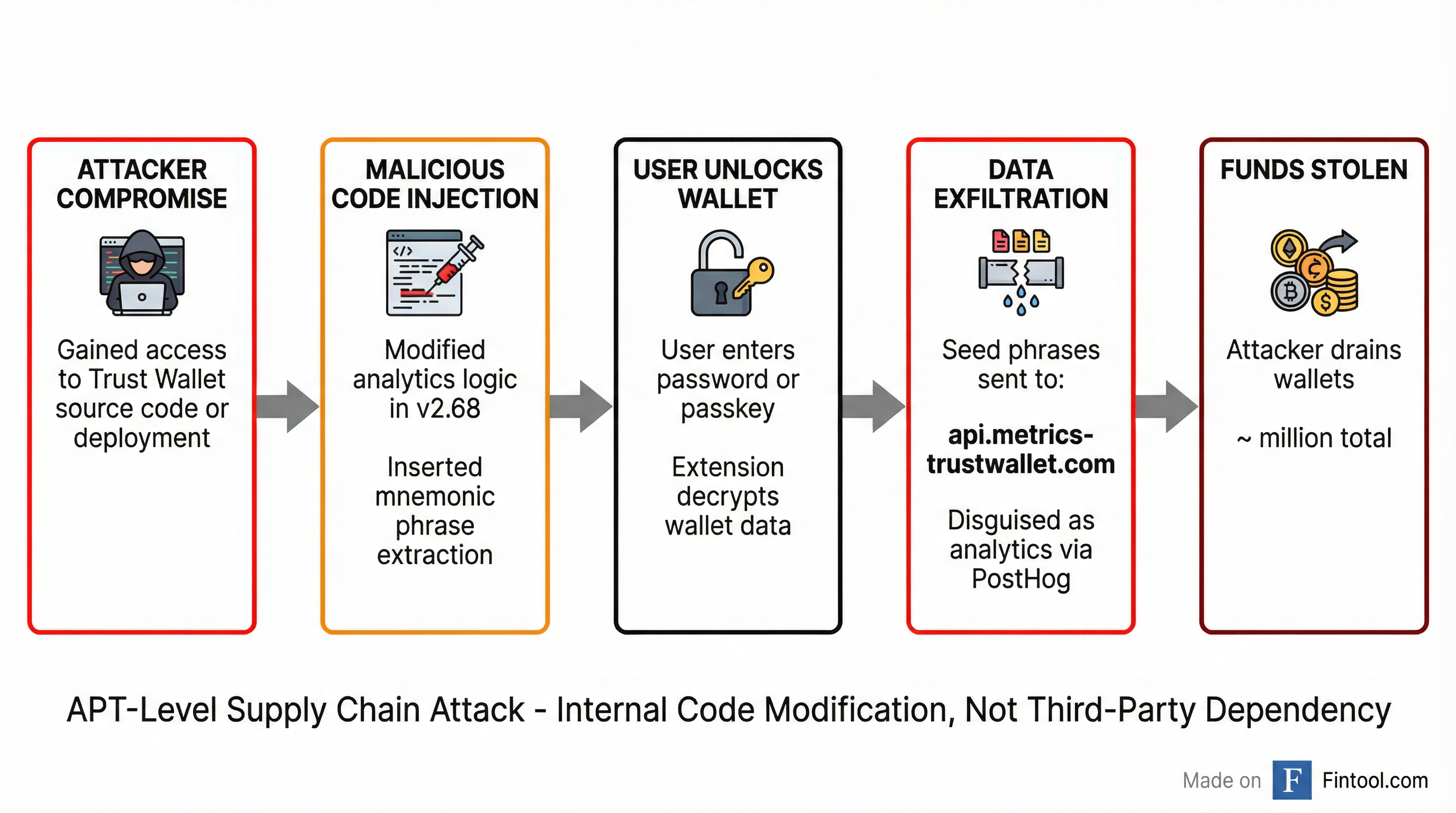
The backdoor operated through three steps:
- Password Interception: When users unlocked their wallet with a password or passkey, the malicious code captured the credentials
- Seed Phrase Extraction: Using the captured password, the code decrypted stored mnemonic phrases via a
GET_SEED_PHRASEfunction call - Covert Exfiltration: The seed phrases were inserted into an
errorMessagefield and transmitted to the attacker's server, camouflaged as legitimate PostHog analytics traffic
The use of PostHog—a legitimate open-source analytics platform that Trust Wallet already employed—made the malicious traffic nearly invisible to standard security monitoring.
"This backdoor incident originated from malicious source code modification within the internal Trust Wallet extension codebase (analytics logic), rather than an injected compromised third-party dependency... We have strong reason to believe this is a professional APT-level attack."
— SlowMist Security Team
Funds Already Moving Through Exchanges
On-chain tracker Lookonchain identified the breakdown of stolen assets: approximately 33 BTC (~$3 million), $3 million in Ethereum and Layer-2 tokens, and roughly $431 in Solana assets.
The attacker has wasted no time laundering the proceeds. As of December 26, approximately $4.25 million has already been routed through instant exchange services including ChangeNOW and FixedFloat, as well as centralized exchanges KuCoin and HTX.
This rapid movement through multiple venues complicates recovery efforts, though frozen funds at centralized exchanges remain potentially recoverable through legal channels.
Binance's Response: Full Reimbursement Pledged
Trust Wallet's parent company moved quickly to contain reputational damage. By December 26, the wallet team had issued an official advisory urging all users to disable version 2.68 immediately and upgrade to the patched version 2.69.
CZ, who remains influential at Binance despite stepping down as CEO in 2023, personally addressed the incident on X:
"Update on the Trust Wallet Browser Extension (v2.68) incident: We've confirmed that approximately $7M has been impacted and we will ensure all affected users are refunded. Supporting affected users is our top priority."
Binance acquired Trust Wallet in July 2018 as its first-ever acquisition, paying a mixture of cash, stock, and BNB tokens. At the time, BNB traded at $14.80—today it hovers near $840. The wallet has since grown to support over 10 million crypto assets across 100+ blockchains, with more than 200 million cumulative downloads.
The Bigger Picture: $3.4 Billion Stolen in 2025
The Trust Wallet breach comes amid a record year for crypto theft. According to Chainalysis's December 2025 report, hackers have stolen over $3.4 billion in cryptocurrency this year, with North Korean state-sponsored groups responsible for $2.02 billion of that total—a 51% increase from 2024.
Personal wallet compromises have surged dramatically. Chainalysis tracked 158,000 individual wallet incidents affecting 80,000 unique victims in 2025, up from 64,000 incidents last year. However, the total value stolen from individuals actually declined to $713 million from $1.5 billion in 2024, suggesting attackers are targeting more users but extracting smaller amounts per victim.
| Metric | 2024 | 2025 | Change |
|---|---|---|---|
| Total Crypto Stolen | $2.2B | $3.4B | +55% |
| North Korea Share | $1.34B | $2.02B | +51% |
| Individual Wallet Incidents | 64,000 | 158,000 | +147% |
| Value from Individual Wallets | $1.5B | $713M | -52% |
Source: Chainalysis 2025 Crypto Crime Report
The Trust Wallet attack represents a concerning evolution: rather than exploiting smart contract vulnerabilities or social engineering individual users, sophisticated actors are now targeting the software supply chain itself.
What Users Should Do Now
Trust Wallet's official guidance for potentially affected users:
- Immediately disconnect your device from the internet before performing any investigation
- Check your extension version in Chrome settings—if running v2.68, disable it immediately
- Export private keys and mnemonic phrases from a safe, isolated device
- Transfer all funds to a new wallet with freshly generated keys
- Upgrade to version 2.69 only on a clean device after securing funds
Mobile-only users are not affected by this incident, as the breach was isolated to the Chrome browser extension.
The Unanswered Question
SlowMist's analysis raises a troubling implication: the attacker "may have already gained control of Trust Wallet-related developer devices or publishing-deployment permissions prior to December 8."
How a malicious build reached Google's Chrome Web Store under an official, trusted brand remains the most uncomfortable question facing both Trust Wallet and the broader crypto ecosystem. The incident underscores that even well-resourced, institutionally-backed crypto products remain vulnerable to supply chain compromises—and that self-custody, while removing counterparty risk, introduces its own attack surface.
For the hundreds of users who lost funds on Christmas Day, CZ's reimbursement pledge offers relief. But the breach serves as a stark reminder: in crypto, security is everyone's responsibility—and even trusted software deserves verification.
Related: